
Complete solution to secure sensitive data from leaking out from endpoints.
Secure each endpoint (desktop, laptop, mobile) by controlling the use of portable devices and allowing/blocking data transfer via group policies.
Dramatically reduce the risks posed by internal threats that could lead to data being leaked, stolen, damaged or otherwise compromised.
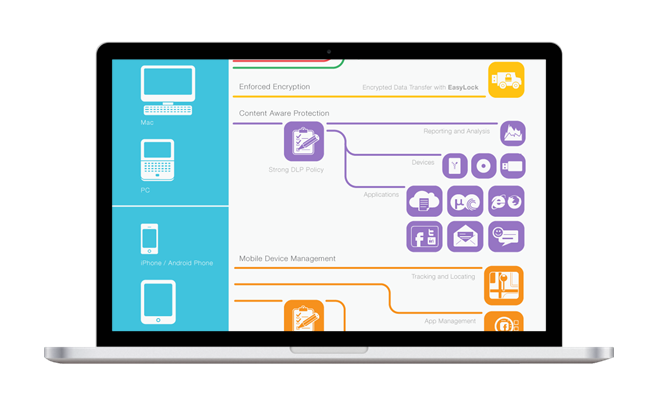
Content Aware Protection
Deep control over sensitive data leaving the endpoints (desktop, laptop, tablet, mobile). Transfer of important company data will be logged & reported, by being aware of the document type (Word, Excel, images, etc.) and content type (sales figures, bank details, credit card info, etc.).
Not only can you block USB drives, you can even block data transfer via copy/paste, web browsers, Skype, Email (Outlook, Thunderbird, Lotus Notes, Webmail, Hotmail, Gmail, etc.), cloud storage (Google drive, Dropbox, etc.).


Centralised control & management
Web based dashboard allows to centrally control the use of removable devices and easily manage & implement data policies on endpoints according to group, department, or employee type. The same web based interface has Administrative & Reporting sections to give real-time information about organization-wide controlled devices and data transfer activity. The Endpoint Protector solution can be deployed as a hardware or virtual appliance and has a quick set up time.

